
КАТЕГОРИИ:
Архитектура-(3434)Астрономия-(809)Биология-(7483)Биотехнологии-(1457)Военное дело-(14632)Высокие технологии-(1363)География-(913)Геология-(1438)Государство-(451)Демография-(1065)Дом-(47672)Журналистика и СМИ-(912)Изобретательство-(14524)Иностранные языки-(4268)Информатика-(17799)Искусство-(1338)История-(13644)Компьютеры-(11121)Косметика-(55)Кулинария-(373)Культура-(8427)Лингвистика-(374)Литература-(1642)Маркетинг-(23702)Математика-(16968)Машиностроение-(1700)Медицина-(12668)Менеджмент-(24684)Механика-(15423)Науковедение-(506)Образование-(11852)Охрана труда-(3308)Педагогика-(5571)Полиграфия-(1312)Политика-(7869)Право-(5454)Приборостроение-(1369)Программирование-(2801)Производство-(97182)Промышленность-(8706)Психология-(18388)Религия-(3217)Связь-(10668)Сельское хозяйство-(299)Социология-(6455)Спорт-(42831)Строительство-(4793)Торговля-(5050)Транспорт-(2929)Туризм-(1568)Физика-(3942)Философия-(17015)Финансы-(26596)Химия-(22929)Экология-(12095)Экономика-(9961)Электроника-(8441)Электротехника-(4623)Энергетика-(12629)Юриспруденция-(1492)Ядерная техника-(1748)
Preventative tips
|
|
|
|

|
|
- The golden rule to avoid being phished is to never ever click the links within the text of the e-mail. Always delete the e-mail immediately. Once you have deleted the e-mail then empty the trash box in your e-mail client as well. This will prevent "accidental" clicks from happening as well.
- To protect your computer system from this type of malicious code, install and use an antivirus program. This utility scans hard disk drives for viruses, worms and Trojan horses and removes, fixes or isolates any threats that are found. Most antivirus programs include an auto-update feature that enables the program to download profiles of new viruses so that it can check for the new viruses on your system as soon as they are discovered.
- Install spam filter and security software that keeps an eye on you while you browse the web.
- Make backup copies of your files regularly.
- Don't accept files from high-risk sources.
- Use a digital certificate, an electronic way of proving your identity, when you are doing
business on the Internet. Avoid giving credit card numbers. - Don't believe everything you read on the Net. Have a suspicious attitude toward its contents.
- Avoid keeping passwords stored on your computer and disclosing them to anybody.
- If you are accessing banking details from a computer that is used by other people, ensure you do not click on "save" password, as another user could gain access.
- Check your bank statements and receipts carefully to ensure there are no fraudulent transactions.
- Set your browser and operating system security level to at least the medium setting (or higher) for best results. You may see a few more warning messages, but it's a small price to pay for security.
- Don't click on any pop-up or advertisement for free anti-spyware software. These are almost always fake, even if they carry the name and logo of a well-known publisher. Ironically, this is a very popular method used to distribute spyware and other malware. If you're looking for anti-virus software, go directly to the company's Web site and be sure you're where you think you are.
- Avoid questionable Web sites. If you visit a site that seems strange, there's a good chance you shouldn't be there.
- When you do download software, read the end user license agreement before committing to the installation. When in doubt, do not install the software.
- Don't download shareware (or anything else for that matter) from unknown sources. Seek out reliable providers of free utilities.
- Make sure you use a firewall - a program designed to prevent spyware from gaining access to the internal network, its job is similar to a physical firewall that keeps a fire from spreading from one area to the next.
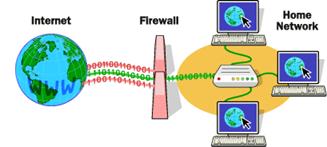
Firewalls use one or more of three methods to control traffic flowing in and out of the network:
Packet filtering - Packets (small chunks of data) are analyzed against a set of filters. Packets that make it through the filters are sent to the requesting system and all others are discarded.
Proxy service - Information from the Internet is retrieved by the firewall and then sent to the requesting system and vice versa.
Stateful inspection - A newer method that doesn't examine the contents of each packet but instead compares certain key parts of the packet to a database of trusted information. Information traveling from inside the firewall to the outside is monitored for specific defining characteristics, then incoming information is compared to these characteristics. If the comparison yields a reasonable match, the information is allowed through. Otherwise it is discarded.
If your computer has already been infected and turned into a zombie computer, there are only a few options open to you. If you have access to tech support who can work on your computer for you, that would be the best option. If not, you can try to run a virus removal program to kill the connection between your computer and the cracker. Unfortunately, sometimes the only option you have is to erase everything on your computer and reload its operating system, then starting from scratch.
Your computer is a great resource. Sadly, crackers think the same thing - they want to make your computer their own resource. If you practice careful Internet habits and follow the abovementioned tips, your chances of your computer remaining secure are very good.
|
|
|
|
|
Дата добавления: 2014-12-27; Просмотров: 782; Нарушение авторских прав?; Мы поможем в написании вашей работы!