
КАТЕГОРИИ:
Архитектура-(3434)Астрономия-(809)Биология-(7483)Биотехнологии-(1457)Военное дело-(14632)Высокие технологии-(1363)География-(913)Геология-(1438)Государство-(451)Демография-(1065)Дом-(47672)Журналистика и СМИ-(912)Изобретательство-(14524)Иностранные языки-(4268)Информатика-(17799)Искусство-(1338)История-(13644)Компьютеры-(11121)Косметика-(55)Кулинария-(373)Культура-(8427)Лингвистика-(374)Литература-(1642)Маркетинг-(23702)Математика-(16968)Машиностроение-(1700)Медицина-(12668)Менеджмент-(24684)Механика-(15423)Науковедение-(506)Образование-(11852)Охрана труда-(3308)Педагогика-(5571)Полиграфия-(1312)Политика-(7869)Право-(5454)Приборостроение-(1369)Программирование-(2801)Производство-(97182)Промышленность-(8706)Психология-(18388)Религия-(3217)Связь-(10668)Сельское хозяйство-(299)Социология-(6455)Спорт-(42831)Строительство-(4793)Торговля-(5050)Транспорт-(2929)Туризм-(1568)Физика-(3942)Философия-(17015)Финансы-(26596)Химия-(22929)Экология-(12095)Экономика-(9961)Электроника-(8441)Электротехника-(4623)Энергетика-(12629)Юриспруденция-(1492)Ядерная техника-(1748)
The ITSM Monitor Control Loop
|
|
|
|
In ITSM, the complex Monitor Control Loop can be represented as shown in Figure 5.4.
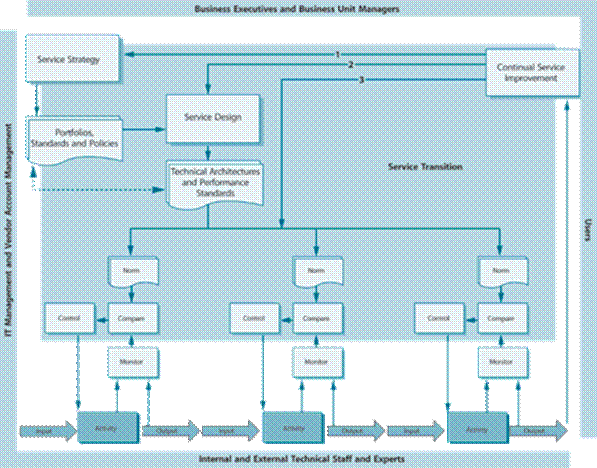
Figure 5.4 ITSM Monitor Control Loop
Figure 5.4 can be used to illustrate the control of a process or of the component s used to deliver a service. In this diagram the word ‘activity’ implies that it refers to a process. To apply it to a service, an ‘activity’ could also be a ‘CI’. There are a number of significant features in Figure 5.4:
- Each activity in a Service Management process (or each component used to provide a service) is monitored as part of the Service Operation processes. The operational team or department responsible for each activity or component will apply the Monitor Control Loop as defined in the process, and using the norms that were defined during the Service Design processes. The role of Operational Monitoring and Control is to ensure that the process or service function s exactly as specified, which is why they are primarily concerned with maintaining the status quo.
- The norms and Monitoring and Control mechanisms are defined in Service Design, but they are based on the standard s and architecture s defined during Service Strategy. Any changes to the organization ’s Service Strategy, architecture, service portfolios or Service Level Requirement s will precipitate changes to what is monitored and how it is controlled.
- The Monitor Control Loop s are placed within the context of the organization. This implies that Service Strategy will primarily be executed by Business and IT Executives with support from vendor account manager s. Service Design acts as the bridge between Service Strategy and Service Operation and will typically involve representatives from all groups. The activities and controls will generally be executed by IT staff (sometimes involving user s) and supported by IT Managers and the vendors. Service Improvement spans all areas, but primarily represents the interests of the business and its users.
- Notice that the second level of monitoring in this complex Monitor Control Loop is performed by the CSI processes through Service Strategy and Service Design. These relationship s are represented by the numbered arrows in Figure 5.4 as follows:
- Arrow 1. In this case CSI has recognized that the service will be improved by making a change to the Service Strategy. This could be the result of the business needing a change to the Service Portfolio, or that the architecture does not deliver what was expected.
- Arrow 2. In this case the Service Level Requirements need to be adjusted. It could be that the service is too expensive; or that the configuration of the infrastructure needs to be changed to enhance performance; or because Operations Management is unable to maintain service quality in the current architecture.
- Arrow 3. In this case the norms specified in Service Design are not being adhered to. This could be because they are not appropriate or executable, or because of a lack of education or a lack of communication. The norms and the lack of compliance need to be investigated and action taken to rectify the situation.
Service Transition provides a major set of checks and balances in these processes. It does so as follows:
- For new services, Service Transition will ensure that the technical architectures are appropriate; and that the Operational Performance Standards can be executed. This in turn will ensure that the Service Operation teams or departments are able to meet the Service Level Requirements.
- For existing services, Change Management will manage any of the changes that are required as part of a control (e.g. tuning) as well as any changes represented by the arrows labelled 1, 2 and 3. Although Service Transition does not define strategy and design services per se, it provides coordination and assurance that the services are working, and will continue to work, as planned.
Why is this loop covered under Service Operation?
Figure 5.4 represents Monitoring and Control for the whole of IT Service Management. Some readers of the Service Operation publication may feel that it should be more suitably covered in the Service Strategy publication.
However, Monitoring and Control can only effectively be deployed when the service is operational. This means that the quality of the entire set of IT Service Management processes depends on how they are monitored and controlled in Service Operation.
The implications of this are as follows:
- Service Operation staff are not the only people with an interest in what is monitored and how they are controlled.
- While Service Operation is responsible for monitoring and control of services and component s, they are acting as stewards of a very important part of the set of ITSM Monitoring and Control loops
- If Service Operation staff define and execute Monitoring and Control procedure s in isolation, none of the Service Management processes or function s will be fully effective. This is because the Service Operation functions will not support the priorities and information requirement s of the other processes, e.g. attempting to negotiate an SLA when the only data available is page-swap rates on a server and detailed bandwidth utilization of a network.
|
|
|
|
|
Дата добавления: 2014-12-23; Просмотров: 560; Нарушение авторских прав?; Мы поможем в написании вашей работы!