
КАТЕГОРИИ:
Архитектура-(3434)Астрономия-(809)Биология-(7483)Биотехнологии-(1457)Военное дело-(14632)Высокие технологии-(1363)География-(913)Геология-(1438)Государство-(451)Демография-(1065)Дом-(47672)Журналистика и СМИ-(912)Изобретательство-(14524)Иностранные языки-(4268)Информатика-(17799)Искусство-(1338)История-(13644)Компьютеры-(11121)Косметика-(55)Кулинария-(373)Культура-(8427)Лингвистика-(374)Литература-(1642)Маркетинг-(23702)Математика-(16968)Машиностроение-(1700)Медицина-(12668)Менеджмент-(24684)Механика-(15423)Науковедение-(506)Образование-(11852)Охрана труда-(3308)Педагогика-(5571)Полиграфия-(1312)Политика-(7869)Право-(5454)Приборостроение-(1369)Программирование-(2801)Производство-(97182)Промышленность-(8706)Психология-(18388)Религия-(3217)Связь-(10668)Сельское хозяйство-(299)Социология-(6455)Спорт-(42831)Строительство-(4793)Торговля-(5050)Транспорт-(2929)Туризм-(1568)Физика-(3942)Философия-(17015)Финансы-(26596)Химия-(22929)Экология-(12095)Экономика-(9961)Электроника-(8441)Электротехника-(4623)Энергетика-(12629)Юриспруденция-(1492)Ядерная техника-(1748)
Fun and games section. How a VIrus infects a program
|
|
|
|
How a virus infects a program
SPEAKING/WRITING PRACTICE SECTION
1. Describe the diagrams.
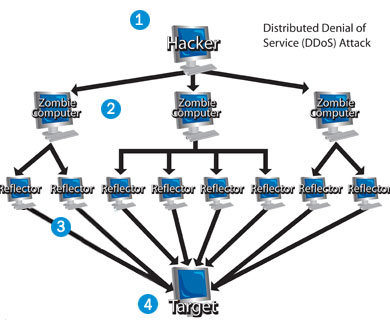
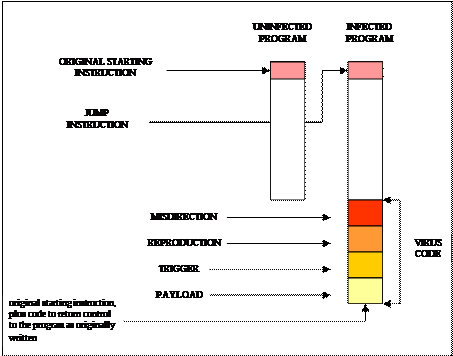

2. Make a report about one or several cyber crimes that are not described in the Key information sections.
3. Make a report on one of the following topics.
The history of hacking. Famous hackers.
Notable computer viruses.
Notable computer criminals.
1. Find the answer to each clue. The first letter has been given in each case.
- A computer system is penetrated by outsiders, and regular users are unable to gain access
- Software scans inbound and outbound email to detect and block any damaging content
- Organizations that work to prevent and investigate crimes, such as the police and the FBI
- This ensures that all people can enjoy access to justice and the freedom of speech
- An informal word meaning to look at something secretly, to discover information
| d | о | s | a | |||||||||||||||||||||
| a | - | v | p | |||||||||||||||||||||
| l | e | a | ||||||||||||||||||||||
| h | r | l | ||||||||||||||||||||||
| s |
2. Solve the anagrams by reading the clues and putting the letters in order to form words. Enter the solutions in the table to find the mystery words. Define the found expression.
1. Software that collects information from computers secretly…………………….…..…YEARSPW
2. Illegal copying and distribution of copyrighted content ………………….………………IYARCP
3. A self-contained and self-copying virus……………………………………………………MRWO
4. What a computer gets when it has caught a virus……….……………………………OIIECFNNT
5. A program that helps computers prevent undesirable access........................................ AIELLWRF
6. Internet crime of obtaining money or possessions……….………………………………….AMCS
7. What dishonest people do with information or money……………………………………..AELTS
8. The law that Internet pirates break…...……………………………………………..YOIPRCTHG
9. A disguised or embedded virus…………………...………………………………………AONJRT
10. What a person doing illegal things on the net is……...………………………………IIALMNRC
11. What viruses do to a computer…………………………………………………………EAAMGD
12. Actions that are against the laws …………………………………………………..…..EAILLLG
13. Software which aims to do harm to computers………………………………………EAARWLM
14. The crime of getting bank information………………………………………………..IIGNHHSP
15. Harmful programs that spread over the net………………………………………………..UIRSV
16. The crime of deceiving people to gain something….……………………….……………UADRF
17. The crime of stealing……………..……………………………………………………….ETTFH
18. A group of letters or numbers that gives access to a system…………...…………...OADRPSSW
|
|
|
|
|
Дата добавления: 2014-12-27; Просмотров: 714; Нарушение авторских прав?; Мы поможем в написании вашей работы!