
КАТЕГОРИИ:
Архитектура-(3434)Астрономия-(809)Биология-(7483)Биотехнологии-(1457)Военное дело-(14632)Высокие технологии-(1363)География-(913)Геология-(1438)Государство-(451)Демография-(1065)Дом-(47672)Журналистика и СМИ-(912)Изобретательство-(14524)Иностранные языки-(4268)Информатика-(17799)Искусство-(1338)История-(13644)Компьютеры-(11121)Косметика-(55)Кулинария-(373)Культура-(8427)Лингвистика-(374)Литература-(1642)Маркетинг-(23702)Математика-(16968)Машиностроение-(1700)Медицина-(12668)Менеджмент-(24684)Механика-(15423)Науковедение-(506)Образование-(11852)Охрана труда-(3308)Педагогика-(5571)Полиграфия-(1312)Политика-(7869)Право-(5454)Приборостроение-(1369)Программирование-(2801)Производство-(97182)Промышленность-(8706)Психология-(18388)Религия-(3217)Связь-(10668)Сельское хозяйство-(299)Социология-(6455)Спорт-(42831)Строительство-(4793)Торговля-(5050)Транспорт-(2929)Туризм-(1568)Физика-(3942)Философия-(17015)Финансы-(26596)Химия-(22929)Экология-(12095)Экономика-(9961)Электроника-(8441)Электротехника-(4623)Энергетика-(12629)Юриспруденция-(1492)Ядерная техника-(1748)
Format of Ethernet frame
|
|
|
|
KEY PRINCIPLES
PURPOSE OF THE WORK
LABOROTORY WORK № 7
REQUIREMENTS TO THE PROTOCOL CONTENT
6.6.1 The name of laboratory work.
6.6.2 Purpose of work.
6.6.3 Results of homework performance.
6.6.4 Short description of the done work.
6.6.5 Conclusions about the done work.
6.6.6 Date, the signature of a student, the remark of a teacher.
THEME: ANALYZER OF PROTOCOLS ETHERPEEK NX
Research of processes of data transmission in the Ethernet network by means of the program analyzer of the EtherPeek protocols on an example of the ARP, ICMP, DHCP and FTP protocols.
The Ethernet technology is now the most widespread technology of local networks. Networks with such technology use a method of multiple access with control carrying and detection of collisions (CSMA/CD, Carrier Sense Multiple Access with Collision Detection). The essence of such method of access to the monochannel consists in the following. All computers connected to a network listen to a condition of the environment of transfer, and any computer can begin data transmission only if channel is free. Having begun transfer, the computer continues to listen to the physical environment about possible emergence of a collision, i.e. collision of a frame transferred to them with frames of other computers which, probably, too began transfer at the same time with this computer. In case of collision detection the computer stops transfer of the frame, sends to a network binary interferential sequence in length 32 bits, serving for collision strengthening for the purpose of its fastest detection by all computers of a network, maintains a casual period, then again starts to listen Wednesday to repeat attempt of transfer of the frame which has got to a collision.
The Ethernet technology works at the second (channel) level of reference model of interrelation of open systems (OSI, Open Systems Interconnection). The legal gateway of data of this level is the frame. Frames of Ethernet happen four various formats among which the Ethernet II format (or Ethernet DIX is most often used; DIX is a reduction from names of three companies – DEC, Intel, Xerox, – together developed Ethernet DIX standard specifications). A format of Ethernet II frames given in Fig. 7.2.1.
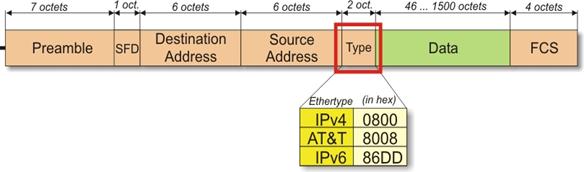
Figure 7.2.1 - Format of Ethernet II frame (DIX)
As is shown in figure 7.2.1: frame consists of the following fields:
- Field the preamble represents sequence from 7 bytes 10101010 and serves for gateway synchronization of the receiver;
- The field SFD, Start of Frame Delimiter – the initial limiter of a frame. Carries out flag function for cyclic synchronization of the receiver. Having received this byte, the receiver understands that the first byte of heading of a frame will be the following byte;
- The address of destination and the address of a source are addresses of a sub-level of management of access to environment (to MAC, Media Access Control) of channel level of structure of the IEEE 802.x standards, or the MAC address.
For simplicity it is possible to consider these addresses as addresses of channel level since, for example, in a format of a Ethernet II frame (DIX) a field of a subtotal of management of the logic channel (LLC, Logical Link Control) is absent. MAC addresses are called as also local, hardware or physical addresses. Unlike MAC addresses, IP addresses are logic and are called as also network addresses. Actually, the MAC address is an address of a network payment of the computer, written down by her producer in ROM. It consists of 48 categories. The structure of the MAC address is shown in fig. 7.2.2.
As we see from figure 7.2.2, the 48-digit MAC address consists of two parts – the 24-digit unique identifier of the organization (OUI, Organizationally Unique Identifier), appointed by IEEE Committee to each producer of the equipment and the 24-categories appointed by the producer to each payment made by it. For example, for the OUI Committee Cisco company appointed OUI 00 60 2F (in a hexadecimal form). Thus, in the greater 24 categories of the MAC address of all network payments made by the Cisco company, there will be a binary combination 0000 0000 0110 0000 0010 1111.

Figure 7.2.2 - MAC address structure
- In the field the type of the protocol is specified the identifier of the protocol of the higher level which has enclosed the package in the data field of a frame. As it was told earlier, the frame is a legal bgateway of data of channel level. In relation to channel network level is higher. Examples of protocols of network level – IP, IPX. For example, if in the data field of a frame the IP package is enclosed, value weeding protocol type in a hexadecimal form – 0800 that identifies the IP protocol.
- In the field data the legal bgateway of data of higher level, for example, an IP package is put. For ensuring reliable recognition of collisions the length of the data field shouldn't be less than 46 bytes. If in the data field the package in length less than 46 bytes is put, the data field is supplemented to 46 bytes in zero or units.
- The control sequence of a frame (FCS, Frame Check Sequence) is 32 bits of a superfluous cyclic code for detection of mistakes.
|
|
|
|
|
Дата добавления: 2014-12-27; Просмотров: 666; Нарушение авторских прав?; Мы поможем в написании вашей работы!